
In the event you were not in attendance at the international legal tech security conference this past week in San Antonio, I wanted to recap an email security breach scenario that we discussed, and please note that breaches like this are hardly limited to the legal industry. As they say, the players (or industry) may change, but the game (sadly) remains the same.
[Major Florida Bar CLE Cybersecurity Webinar Sponsored by RPost with 1 Full Free Credit: October 18. Learn More]
The key to making this email scam work has been the key to literally all confidence scams since the beginning of time: build a relationship. Using the legal industry example, let’s imagine that a cybercriminal operating outside of your legal jurisdiction (let’s say Ray) sends an email from what could be a potential big corporate client (let’s say a household name fast food chain). Using LinkedIn or other recruiter tools, it could take less than 10 minutes to know who your potential clients could be as well as your corporate reporting structure.
The cybercriminal finds your contact info and sends an email from the address ray@ BurgerKing.com saying that he would like to retain you/your firm’s legal services for an important and time-sensitive matter and to send over the firm’s retainer letter. You look on LinkedIn and you see that Ray is an associate general counsel at Burger King — so you respond with some gusto, thinking you are about to reel in a mega client. Your reply, however, populates ray@ BergerKing.com in the reply to field (due to some sly email formatting tricks) so the reply is routed to a cybercriminal posing as Ray. But, the difference in the domains are imperceivable, especially in the heat of the new client onboarding excitement.
After receiving the letter from you, Ray (fake Ray) then replies with some inane comments about the weather and redlines to your engagement agreement—standard stuff. Beneath the surface though, he has embedded a virus via a package file that grants access to your machine. You open the file despite warnings from your existing email system—after all this email came from someone at Burger King, and you grew up on their burgers! Your email account and perhaps other systems are now compromised, which can set the stage for “real” emails going out from your firm soliciting payments that will never materialize for you.
Scams like this one are growing in frequency. According to one lawyer friend of mine, this is now happening so much that his firm must waste internal resources trying to chase down other contacts at the inquiring company to engage services just to ensure that it is a legitimate potential of new business before any engagement documentation is sent.
RMail’s new Microsoft Outlook integrated Lookalike Domain Alert™ feature is the only easy way to thwart this type of scam, thus saving you and your firm a lot of headaches. It would have seen via AI that the “BergerKing” in the reply domain was a lark and not one that you have any business contacting.
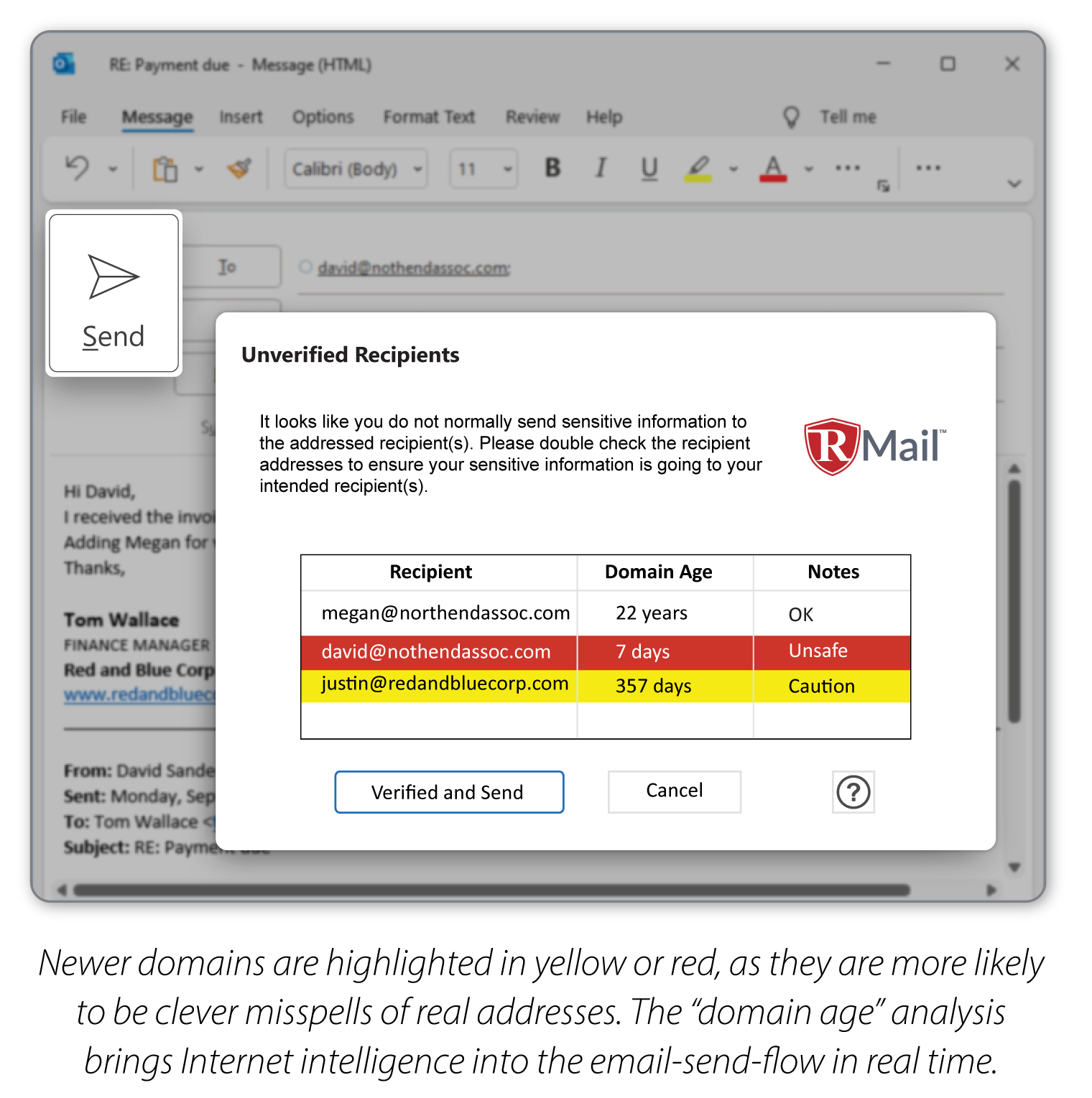
And, what is really impressive, is that this Lookalike Domain alert technology runs inside the RMail for Microsoft Outlook add-in, so there is no fancy set up or expensive service that you need to use it. A 2-minute installation (click here to download free) and you are protected.
So, think of RMail as SMARTR outbound email security – key layers to defend against targeted email-based cyberattacks. RMail does what no other email security server or secure email gateway does – not even Microsoft, and it can be had via a simple add-in to Outlook or Gmail – or with an outbound email connection to the RMail Gateway.
Please contact us to learn more about RMail and its Lookalike Domain Alert™ feature. Also, we’d like to ensure you have heard about – and been invited to – RPost’s Optimize!2022 global e-security and e-sign user conference (click here to read more). This year’s unique format includes web sessions spaced throughout the month plus in-person expert tours across the Americas and Europe.

April 25, 2025

April 17, 2025

April 11, 2025

April 04, 2025

March 28, 2025